Navigating the Complexities of Network Security: A Comprehensive Guide to Ingress Checkpoints
Related Articles: Navigating the Complexities of Network Security: A Comprehensive Guide to Ingress Checkpoints
Introduction
With great pleasure, we will explore the intriguing topic related to Navigating the Complexities of Network Security: A Comprehensive Guide to Ingress Checkpoints. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Navigating the Complexities of Network Security: A Comprehensive Guide to Ingress Checkpoints
- 2 Introduction
- 3 Navigating the Complexities of Network Security: A Comprehensive Guide to Ingress Checkpoints
- 3.1 Understanding Ingress Checkpoints: A Gateway to Security
- 3.2 The Benefits of Implementing Ingress Checkpoints
- 3.3 Implementing Ingress Checkpoints: A Practical Guide
- 3.4 The Role of Ingress Checkpoints in Modern Security Architectures
- 3.5 FAQs About Ingress Checkpoints
- 3.6 Tips for Implementing Effective Ingress Checkpoints
- 3.7 Conclusion: Embracing a Multi-Layered Approach to Network Security
- 4 Closure
Navigating the Complexities of Network Security: A Comprehensive Guide to Ingress Checkpoints

In the ever-evolving landscape of cybersecurity, organizations face a relentless barrage of threats. From sophisticated malware to targeted attacks, securing sensitive data and maintaining operational integrity requires robust defenses. One crucial element in this defense strategy is the implementation of ingress checkpoints, a vital component of network security that effectively acts as a gatekeeper, scrutinizing incoming traffic and preventing unauthorized access.
This comprehensive guide delves into the intricacies of ingress checkpoints, exploring their purpose, benefits, and practical applications. Understanding ingress checkpoints is essential for organizations seeking to bolster their security posture, mitigate risks, and ensure the smooth functioning of their network infrastructure.
Understanding Ingress Checkpoints: A Gateway to Security
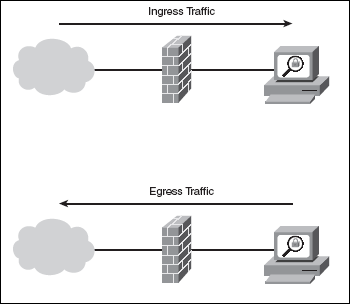
An ingress checkpoint, in essence, acts as a security filter, meticulously examining all incoming traffic before granting access to the network. Imagine it as a highly sophisticated security guard at the entrance of a building, meticulously scrutinizing each visitor before granting entry. This checkpoint is implemented at the network perimeter, the point where external networks attempt to connect to the organization’s internal systems.
The core function of an ingress checkpoint is to enforce security policies, ensuring that only authorized and trusted traffic is allowed to enter the network. This involves meticulously inspecting incoming data packets, verifying their origin, destination, and content. By carefully analyzing this information, the ingress checkpoint can identify and block malicious traffic, including:
- Malware: Malicious software designed to infiltrate and compromise systems.
- Exploits: Vulnerability exploits aiming to gain unauthorized access.
- Denial-of-service attacks: Attempts to overwhelm network resources and disrupt services.
- Data breaches: Unauthorized access to sensitive information.
The Benefits of Implementing Ingress Checkpoints
Implementing ingress checkpoints offers a multitude of benefits, significantly enhancing an organization’s security posture and mitigating potential threats. These benefits include:
1. Enhanced Network Security: By acting as a robust barrier against unauthorized access, ingress checkpoints provide a critical layer of protection, safeguarding the network from malicious actors.
2. Reduced Attack Surface: By carefully scrutinizing incoming traffic, ingress checkpoints effectively reduce the attack surface, minimizing the potential points of entry for malicious actors.
3. Improved Compliance: In an era of stringent data privacy regulations, ingress checkpoints help organizations comply with industry standards and legal requirements by ensuring data integrity and secure access.
4. Enhanced Visibility: Ingress checkpoints provide valuable insights into network traffic patterns, enabling security teams to monitor activities, identify potential threats, and proactively address vulnerabilities.
5. Streamlined Security Management: By centralizing security controls, ingress checkpoints simplify the management of security policies, reducing the complexity of managing multiple security tools.
6. Reduced Risk of Data Breaches: By effectively blocking malicious traffic, ingress checkpoints significantly reduce the risk of data breaches, safeguarding sensitive information and maintaining business continuity.
7. Improved Network Performance: By filtering out malicious traffic, ingress checkpoints can enhance network performance by reducing the burden on network resources and minimizing the impact of security threats.
Implementing Ingress Checkpoints: A Practical Guide
Implementing ingress checkpoints requires a strategic approach, encompassing a combination of hardware, software, and configuration settings. The process typically involves:
1. Defining Security Policies: Establishing clear and comprehensive security policies is paramount. These policies should outline the acceptable traffic types, the level of scrutiny for incoming connections, and the actions to be taken in case of suspicious activity.
2. Selecting the Right Tools: A wide range of security tools are available, each offering unique capabilities and functionalities. Choosing the right tools depends on the specific needs of the organization, the size of the network, and the level of security required.
3. Configuring the Ingress Checkpoint: Once the tools are selected, they need to be carefully configured to align with the defined security policies. This includes setting up rules, defining access controls, and configuring security settings to ensure optimal protection.
4. Monitoring and Maintenance: Regular monitoring and maintenance are crucial to ensure the effectiveness of ingress checkpoints. This involves analyzing logs, identifying potential threats, updating security policies, and patching vulnerabilities.
5. Training and Awareness: Organizations should invest in training their IT staff on the intricacies of ingress checkpoints, enabling them to effectively manage and maintain these security measures.
The Role of Ingress Checkpoints in Modern Security Architectures
Ingress checkpoints play a vital role in modern security architectures, serving as a critical component of a multi-layered defense strategy. They are often integrated with other security tools, including firewalls, intrusion detection systems, and antivirus software, forming a comprehensive security ecosystem.
1. Firewalls: Firewalls act as the first line of defense, filtering traffic based on predefined rules. Ingress checkpoints complement firewalls by providing deeper inspection of traffic, identifying more sophisticated threats.
2. Intrusion Detection Systems (IDS): IDS systems actively monitor network traffic for suspicious patterns and alert security teams to potential threats. Ingress checkpoints enhance IDS systems by providing valuable insights into the nature of incoming traffic, enabling more accurate threat detection.
3. Antivirus Software: Antivirus software protects endpoints from malware infections. Ingress checkpoints prevent malicious software from entering the network, reducing the risk of endpoint infections.
FAQs About Ingress Checkpoints
1. What is the difference between an ingress checkpoint and a firewall?
While both ingress checkpoints and firewalls act as security barriers, they differ in their scope and functionality. Firewalls primarily focus on blocking traffic based on pre-defined rules, while ingress checkpoints provide deeper inspection of traffic, analyzing content and identifying more sophisticated threats.
2. Are ingress checkpoints necessary for all organizations?
The need for ingress checkpoints depends on the organization’s size, industry, and the sensitivity of the data being protected. Organizations handling sensitive data, critical infrastructure, or facing significant security risks should consider implementing ingress checkpoints.
3. How do I choose the right ingress checkpoint solution?
Selecting the right ingress checkpoint solution depends on the specific needs of the organization, including the size of the network, the level of security required, and the budget. It’s essential to evaluate different solutions, consider their capabilities, and choose the one that best aligns with the organization’s requirements.
4. What are the potential challenges of implementing ingress checkpoints?
Implementing ingress checkpoints can pose certain challenges, including the complexity of configuration, the need for ongoing maintenance, and the potential impact on network performance. Careful planning, thorough testing, and ongoing monitoring can mitigate these challenges.
5. How can I ensure the effectiveness of my ingress checkpoint solution?
Regular monitoring, performance testing, and security audits are crucial to ensure the effectiveness of ingress checkpoint solutions. It’s essential to stay updated on emerging threats, patch vulnerabilities, and adapt security policies as needed.
Tips for Implementing Effective Ingress Checkpoints
1. Define Clear Security Policies: Establish comprehensive security policies that clearly outline acceptable traffic types, access controls, and actions to be taken in case of suspicious activity.
2. Conduct Thorough Testing: Before deploying an ingress checkpoint solution, conduct thorough testing to ensure its effectiveness, validate its configuration, and minimize potential performance impacts.
3. Implement Strong Authentication: Utilize multi-factor authentication to enhance security and prevent unauthorized access to the network.
4. Stay Updated on Security Threats: Regularly monitor security threat intelligence feeds and update security policies and configurations to address emerging threats.
5. Invest in Training: Provide IT staff with comprehensive training on the intricacies of ingress checkpoints, enabling them to effectively manage and maintain these security measures.
Conclusion: Embracing a Multi-Layered Approach to Network Security
In today’s digital landscape, organizations face an unprecedented level of security threats. Implementing ingress checkpoints is a crucial step in building a robust and comprehensive security architecture. By meticulously scrutinizing incoming traffic, enforcing security policies, and enhancing visibility, ingress checkpoints effectively safeguard sensitive data, mitigate risks, and ensure the smooth functioning of network infrastructure.
However, it’s crucial to remember that ingress checkpoints are just one component of a multi-layered security approach. Combining them with other security tools, such as firewalls, intrusion detection systems, and antivirus software, creates a comprehensive defense strategy that can effectively protect against a wide range of threats. By embracing a holistic approach to security, organizations can navigate the complexities of the digital landscape and ensure the integrity of their critical systems.






Closure
Thus, we hope this article has provided valuable insights into Navigating the Complexities of Network Security: A Comprehensive Guide to Ingress Checkpoints. We appreciate your attention to our article. See you in our next article!